In this article, We will learn the k8s authentication mechanism using X509 Certificate.
Authentication is the process of validating the user by k8s API-Server.
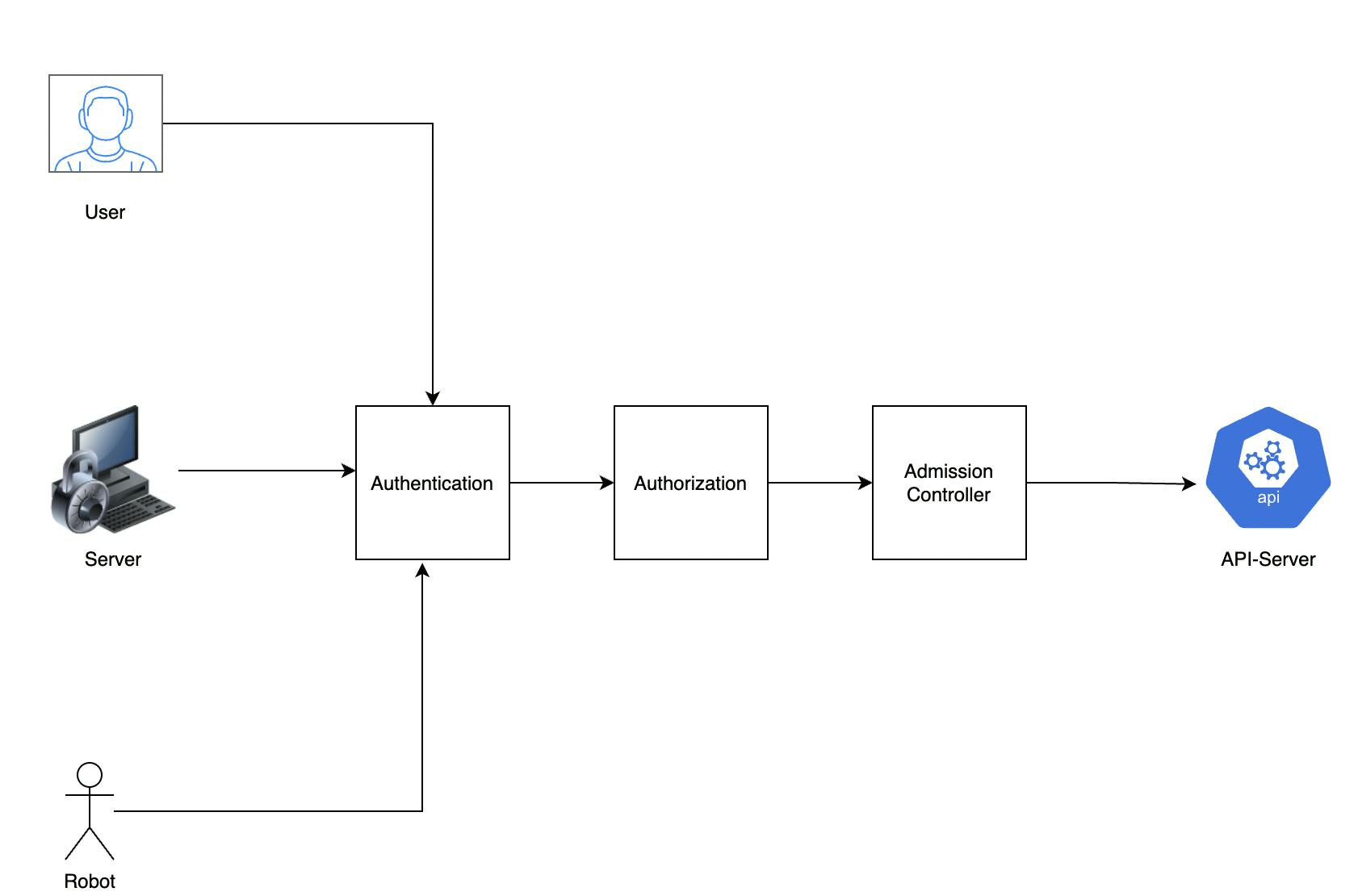
In k8s, Users can be authenticated by the below strategy.
X509 Certificate
Bearer token
Third-Party Authentication mechanisms like LDAP, Kerberos, git etc..,
TLS Certificate:
Here, I have explained internally how authentication works.

Let's start a practice without any delay.
Step 1: Copy API Server's ca.crt and ca.key to local machine
ubuntu@kubemaster:~$ kg nodes
NAME STATUS ROLES AGE VERSION
kubemaster Ready control-plane 4d2h v1.26.4
kubeworker01 Ready <none> 4d2h v1.26.4
ubuntu@kubemaster:~$
ubuntu@kubemaster:/etc/kubernetes/pki$ ls | grep -i ca.
ca.crt
ca.key
ubuntu@kubemaster:/etc/kubernetes/pki$
arun@Aruns-MacBook-Air k8s_cert % ls #copied to local machine
ca.crt ca.key
arun@Aruns-MacBook-Air k8s_cert %
Step 2: Generate public and private key for user's using openssl
openssl genrsa -out developer.key 2048
openssl req -new -key developer.key -out developer.csr -subj "/CN=developer/O=dev/O=infy"
sudo openssl x509 -req -in developer.csr -CA /etc/kubernetes/pki/ca.crt -CAkey /etc/kubernetes/pki/ca.key -CAcreateserial -out developer.crt -days 30
openssl genrsa -out devops.key 2048
openssl req -new -key devops.key -out devops.csr -subj "/CN=devops/O=devops/O=infy"
sudo openssl x509 -req -in devops.csr -CA /etc/kubernetes/pki/ca.crt -CAkey /etc/kubernetes/pki/ca.key -CAcreateserial -out devops.crt -days 30
openssl genrsa -out infra.key 2048
openssl req -new -key infra.key -out infra.csr -subj "/CN=infra/O=infra/O=infy"
sudo openssl x509 -req -in infra.csr -CA /etc/kubernetes/pki/ca.crt -CAkey /etc/kubernetes/pki/ca.key -CAcreateserial -out infra.crt -days 30
CN - Common Name
O - Organization
Step 3: Add User Configurations in kubeconfig file
#developer
k config set-credentials developer --client-key=developer.key --client-certificate=developer.crt
k config set-context developer@kubernetes --cluster=kubernetes --user=developer
k config use-context developer@kubernetes
#devops
k config set-credentials developer --client-key=devops.key --client-certificate=devops.crt
k config set-context devops@kubernetes --cluster=kubernetes --user=devops
k config use-context devops@kubernetes
#infra
k config set-credentials infra --client-key=infra.key --client-certificate=infra.crt
k config set-context infra@kubernetes --cluster=kubernetes --user=infra
k config use-context infra@kubernetes
Reference: